Following our previous article, "Block ads, stay clean", this time we look at a more elaborate scheme to compromise your computer: "ClickFixing" - luring you into executing a very simple string of copy/paste-like tasks to install malware on your computer*. Ready to be lured?
Patient zero of such attacks was a fake website called "github-scanner.com", allegedly linked to the GitHub Security Team. While the genuine GitHub scanners are available directly on the GitHub site (and similar scanners are deployed within the CERN GitLab instance), "github-scanner" is entirely fake and has just one purpose: to get your clicks. To get your copy & paste. It starts with a CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) like the one on the left below but, unlike other CAPTCHAs, which usually ask you to identify cars, bikes or cross-walks on images, this CAPTCHA takes a different path. An evil path. A path not to be followed (see the image on the right; images from SANS).
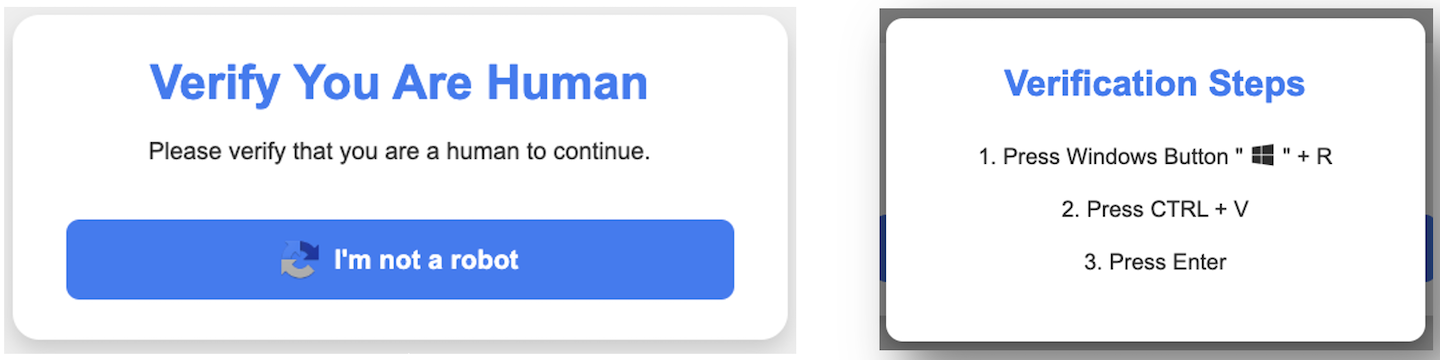
Windows-philes will quickly see that instruction (1.) opens a dialog to run a command. A command which is hidden when you click Control+V in step (2.) and execute it with (3.) "Enter". And with that "Enter" your Windows system has been successfully attacked. Compromised. Malwared. Gone.
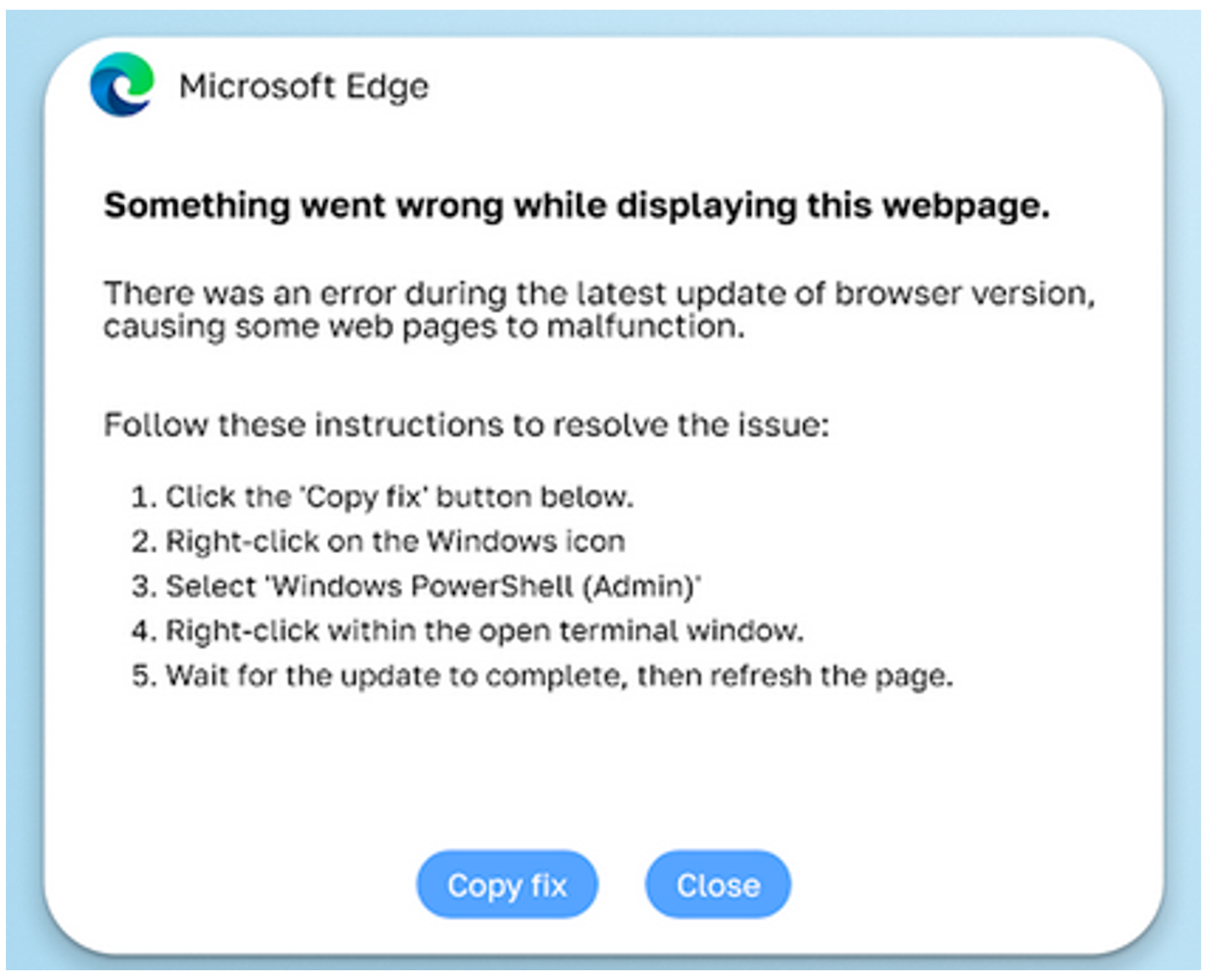
Since then, fake CAPTCHA pages have become an increasingly popular way for attackers to take over (Windows) systems. Variations on that scheme have displayed fake browser update prompts like the one below (from keep aware):
So, what now? STOP - THINK - DON'T CLICK! is surely the best mantra ever. Running an ad blocker is surely another good practice. Check out our previous Bulletin article!






