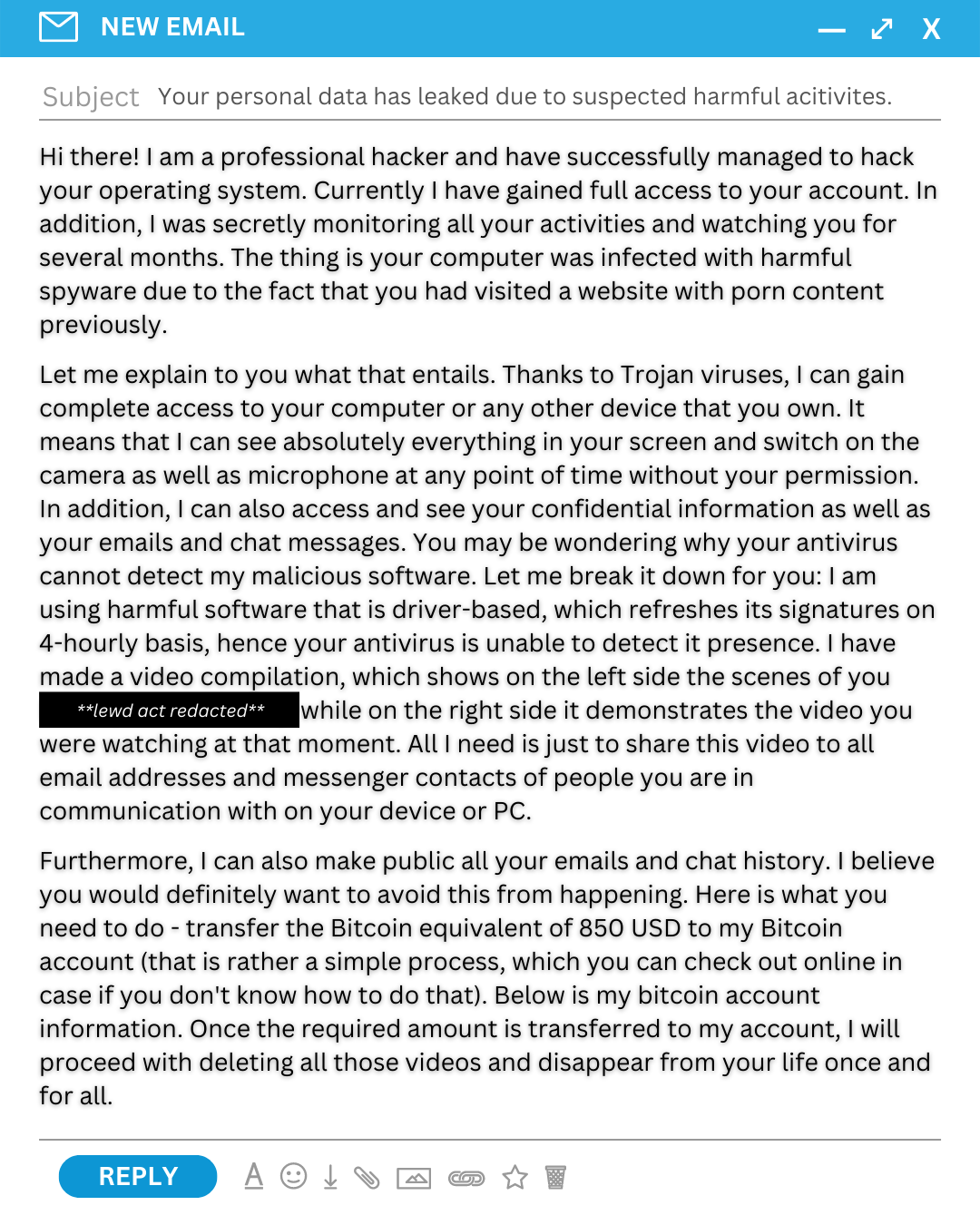
Extortion emails threatening the recipient that embarrassing information will be made public unless they pay up are on the rise.
Sergeant David Mitchell from South Australia Police's Cybercrime Investigation Section said victims receive an email from someone claiming to be a professional hacker who claims to have gained access to accounts and is monitoring activities.
"The hacker claims they gained access to the victim's operating system and been watching them for months," Sergeant Mitchell said.
"They also state they have embarrassing information, chat histories, images and vision of the person using their computer, they then often ask victims to make payments in money transfers or cryptocurrency."
If you have received an extortion email message -
- Do not panic. It is unlikely these individuals have any compromising video of you.
- Do not transfer any money or cryptocurrency.
- If the password included in the email is a password you recognise, change your password for any account where it has been used.
- Do not reply and do not click on any links.
- Be aware that the scammer has the ability to make the email appear as if it has come from your own email address. Delete the email immediately.
If you are a victim of this cybercrime you are encouraged to make a report at https://www.cyber.gov.au/acsc/report
For further information on scams affecting South Australians, please visit http://www.police.sa.gov.au/scams
Risk Warning: Cryptocurrency is a unregulated virtual notoriously volatile instrument with a high level of risk. Any news, opinions, research, data, or other information contained within this website is provided for news reporting purposes as general market commentary and does not constitute investment or trading advice.






