With the roll-out of 2-factor authentication (2FA) for the CERN Single Sign-On (SSO) now concluded - thank you all for helping to secure CERN! - the next step required by the 2023 CERN cybersecurity audit is to streamline all methods for remotely connecting to CERN and ensure that they are all properly 2FA-protected using the same means as the CERN SSO, i.e. your smartphone app or your hardware dongle (e.g. a YubiKey or a fingerprint reader). In parallel, any remote access to the Technical Network (TN) used for accelerator controls and CERN's infrastructure will require 2FA protection, too. How do we plan to do this?
For remote logins to CERN, i.e. logins from the internet, there must always be three main possibilities: via the CERN SSO towards any CERN web service, via CERN's Windows Terminal Servers ("CERNTS"), and via the interactive Linux cluster LXPLUS. Additionally, the AIADM cluster permits dedicated access for data centre managers in order to administer IT services, and the Remote Operations Gateways (ROGs) provide direct remote access to the TN for control system experts. While the latter two, AIADM and ROG, are already 2FA-protected, the Windows Terminal Servers and LXPLUS are not. But that will change in the coming months in order to fulfil the recommendation of the 2023 CERN cybersecurity audit.
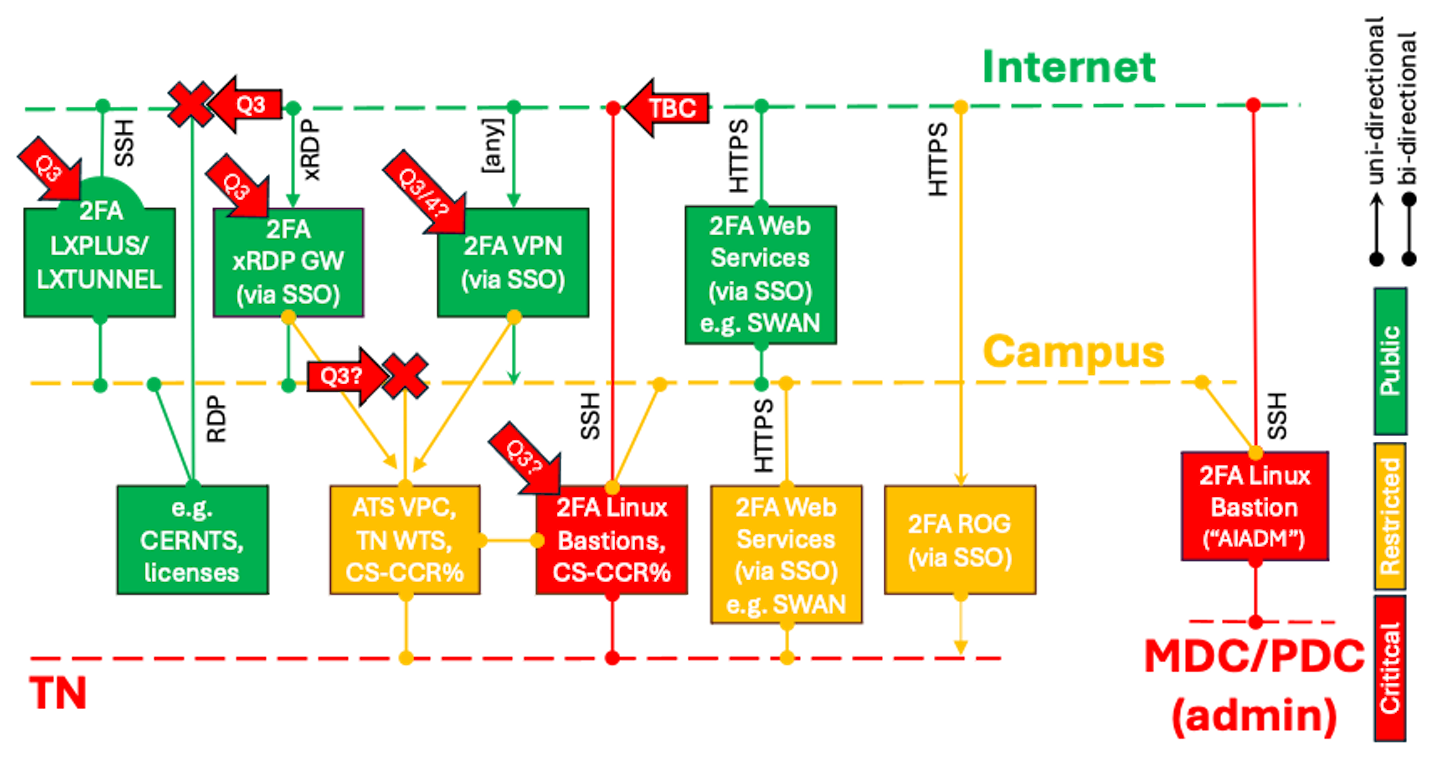
For LXPLUS, based on the experience with AIADM, 2FA-protection will be integrated into the SSH login process (the so-called Pluggable Authentication Module (PAM)). As on AIADM, for every remote login, PAM will ask you to either enter the six-digit number from your smartphone app or push the button on your hardware dongle. Easy as pie as on the CERN SSO. But SSH is not a persistent communication protocol. That means that you would need to log in again as soon as your SSH client loses connection, your device changes IP address or your Wi-Fi signal is lost. With 1FA, that does not matter too much: your SSH key or your Kerberos token come to your rescue or you have to type your password again. With 2FA, it is imperative that you provide your 2FA again. While pushing your YubiKey button again might be less of an issue, typing a different six-digit code over and over again might be (or perhaps not, as it worked for the 600+ AIADM users). The IT department is trying to improve this, but every road taken here is rocky.
For CERNTS, 2FA deployment turned out to be more complicated as Microsoft does not easily allow its login process to be tweaked. Enter the "Windows Remote Desktop Access" solution: any access to CERN's Windows Terminal Server (WTS) cluster (e.g. CERNTS) and their internal equivalents (e.g. the WTS leading to the Technical Network) will in future require connection-by-connection authorisation to be obtained via a Single Sign-On (and hence 2FA) protected webpage - the "Windows Remote Desktop Access" webpage. If you are already logged into the SSO, this is just one additional click. Otherwise, it requires the usual 2FA SSO login before you can use RDP in your WTS. A pilot has been put in production. Let us know what you think!
For the Technical Network (TN), consolidation work has begun in collaboration with the BE system administrators (more on this "TN v3.0" in a future Bulletin article). While the current established solutions - ROG and the dedicated AITNADM Linux gateway - are already using 2FA, the dedicated WTS in the TN and the numerous virtual PCs (VPCs) "trusted" by the TN for development and testing are not. While AITNADM should be extended to 2FA-protect SSH access to those VPCs, their XRDP access and the RDP access to any TN WTS will be subject to the Window Remote Desktop Access webpage mentioned above. One (more) click for the protection of your work and CERN's accelerator complex.
Hence, for the TN the solutions are simple: for web-based control systems, ROG is your friend. Using SSH, you connect to the TN or a VPC via the established AITNADM gateway. And for any Remote Desktop connection to CERNTS or any other dedicated Windows Terminal Server as well as the XRDP session on your VPC, the new Windows Remote Desktop Access Gateway mentioned above will be your 2FA-protected entry point: before connecting you will need to request access via a dedicated webpage granting you a five-minute window to log in.
In parallel, CERN IT is also checking on that big elephant in the data centre: the industrial standard called VPN (virtual private networks). Actually, CERN has already been running a 2FA-protected VPN service since COVID times to allow teleworkers to connect to CERN's otherwise internal licence servers, to the DFS file system and to the ESET antivirus installation servers. Soon, this spontaneous VPN service will be reduced to serve the licence service only (DFS and ESET remain accessible when at CERN). In parallel, the IT department is investigating whether to extend this to a fully fledged VPN service based on either PaloAltoVPN or eduVPN and then to open it up so that it can be used to remotely connect to any other service within CERN, e.g. to LXPLUS, thus providing the mechanism for a persistent connection that has been missing so far, or even to the Campus network.
To sum up, the IT department is currently piloting three solutions: 2FA-LXPLUS for Linux/SSH users, 2FA-Windows Remote Desktop Access Gateway for the Windows-phile, and, eventually, 2FA-VPN for persistent access to the Campus network. While there is no silver bullet for one unique access method, we believe that they still strike an adequate balance between your convenience, CERN's operations and improved security of CERN's accelerator control systems and IT services. Let us have your feedback!






